Compliance¶
Prowler allows you to execute checks based on requirements defined in compliance frameworks. By default, it will execute and give you an overview of the status of each compliance framework:
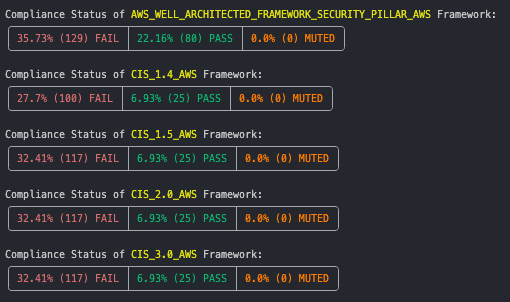
You can find CSVs containing detailed compliance results inside the compliance folder within Prowler's output folder.
Execute Prowler based on Compliance Frameworks¶
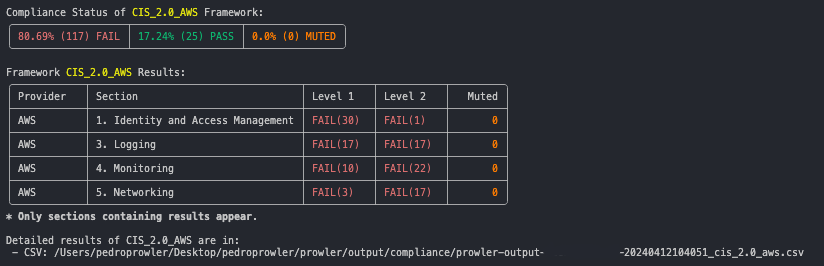
Prowler can analyze your environment based on a specific compliance framework and get more details, to do it, you can use option --compliance:
List Available Compliance Frameworks¶
In order to see which compliance frameworks are cover by Prowler, you can use option --list-compliance:
aws_account_security_onboarding_awsaws_audit_manager_control_tower_guardrails_awsaws_foundational_security_best_practices_awsaws_well_architected_framework_reliability_pillar_awsaws_well_architected_framework_security_pillar_awscis_1.4_awscis_1.5_awscis_2.0_awscis_2.0_gcpcis_2.0_azurecis_2.1_azurecis_3.0_awscis_1.8_kubernetescisa_awsens_rd2022_awsfedramp_low_revision_4_awsfedramp_moderate_revision_4_awsffiec_awsaws_foundational_technical_review_awsgdpr_awsgxp_21_cfr_part_11_awsgxp_eu_annex_11_awshipaa_awsiso27001_2013_awsmitre_attack_awsnist_800_171_revision_2_awsnist_800_53_revision_4_awsnist_800_53_revision_5_awsnist_csf_1.1_awspci_3.2.1_awsrbi_cyber_security_framework_awssoc2_aws
List Requirements of Compliance Frameworks¶
For each compliance framework, you can use option --list-compliance-requirements to list its requirements:
Example for the first requirements of CIS 1.5 for AWS:
Listing CIS 1.5 AWS Compliance Requirements:
Requirement Id: 1.1
- Description: Maintain current contact details
- Checks:
account_maintain_current_contact_details
Requirement Id: 1.2
- Description: Ensure security contact information is registered
- Checks:
account_security_contact_information_is_registered
Requirement Id: 1.3
- Description: Ensure security questions are registered in the AWS account
- Checks:
account_security_questions_are_registered_in_the_aws_account
Requirement Id: 1.4
- Description: Ensure no 'root' user account access key exists
- Checks:
iam_no_root_access_key
Requirement Id: 1.5
- Description: Ensure MFA is enabled for the 'root' user account
- Checks:
iam_root_mfa_enabled
[redacted]
Create and contribute adding other Security Frameworks¶
This information is part of the Developer Guide and can be found here: https://docs.prowler.cloud/en/latest/tutorials/developer-guide/.